Symmetric vs Asymmetric Encryption
Types of Encryption:
Symmetric vs Asymmetric Encryption
What is Encryption and Why Is It Necessary?
Encryption is the process of turning plaintext data into a scrambled format — so that no unauthorized entity can see what the original data was — through the use of a cryptographic key. But that’s not the only benefit of using different types of encryption — it can also help you to protect the integrity of your data, software, communications, and be compliant with some data security and privacy laws and regulations.
Encryption is useful for protecting a variety of personally identifiable information (PII), financial data, intellectual property, and other proprietary information such as:
- Names
- Social security numbers
- Contact information
- Credit card information
- Financial account information
- Credentials
- Technical specs, research, and other sensitive data
Regardless of which type of encryption you’re looking at, it’s going to require a digital key. A cryptographic key is a string of randomly generated characters that’s part of an encryption algorithm. If you compare the process of encryption to locking the door of your home, then the door lock mechanism becomes the encryption, and your physical key becomes the encryption key.
However, encryption differs from physical locks in terms of the use of the keys: In encryption, the same key that encrypted the data may or may not be used to decrypt it. This is an example of the difference between symmetric encryption and asymmetric encryption — the two types of encryption we’ll discuss in this article.
Breaking Down Encryption Types
Symmetric Encryption
In simple terms, symmetric encryption is the simpler and conventional method of securing data. The reason why it’s called “symmetric” is that it’s a process that involves the use of one key by all communicating parties to encrypt and decrypt the data.
Here’s visual breakdown of this method:
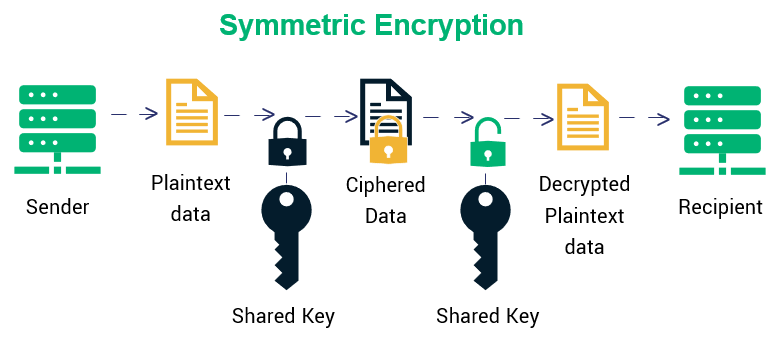
Advantages & Disadvantages of Symmetric Encryption
The most significant advantage when it comes to the symmetric encryption method is its simplicity. As it has only one key doing encryption and decryption, symmetric encryption algorithms are considered the fastest of the two types of encryption and require less computational power to perform.
However, the simplicity of symmetric encryption algorithms isn’t perfect — it has an issue known as “key distribution.” In the case of Bob and Alice, symmetric encryption works just fine as there are only two entities: a sender and a receiver. But what if Alice is gathering information from thousands of sources? If she gives the same key to all of her agents, every piece of data then becomes vulnerable if the key somehow gets exposed. And if Alice gives different symmetric keys to everyone, it means that she must manage thousands of keys, which isn’t a practical thing to do.
When you apply this concept to the millions of communications that take place daily between clients (web browsers) and web servers (websites), you’ll realize just how impractical that can be on a large scale.
Asymmetric Encryption
Asymmetric encryption, as you can guess by its name, involves the use of multiple keys for data encryption and decryption. To be exact, the asymmetric encryption method comprises two encryption keys that are mathematically related to each other. These keys are known as the public key and private key. As a result, the asymmetric encryption method is also known as “public key cryptography.”
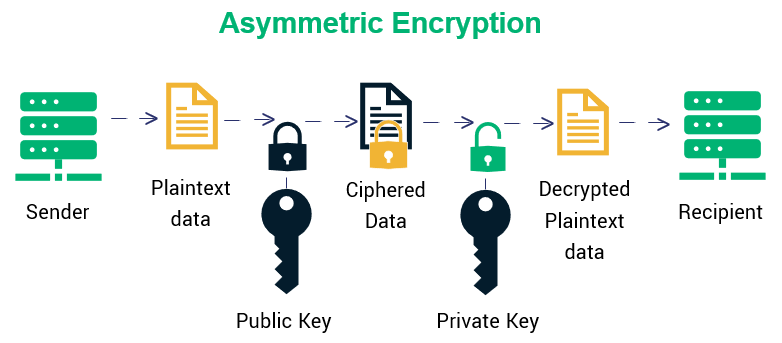
Advantages and Disadvantages of Asymmetric Encryption
The reason why asymmetric encryption had to be invented was to solve the key distribution problem that arises in the case of the symmetric encryption method. Therefore, in the case of Bob and Alice, even if the enemies have Bob’s public key, they won’t be able to decipher the information as it can only be decrypted using Alice’s private key. Not only that, but public key cryptography also solves the key management problem even if Alice is getting information from millions of sources. All she has to do is to secure and manage the private key.
However, like most things in our world, everything comes with a price — and asymmetric encryption is no different. In this case, that price tag comes in the form of decreased speed and computational power as this encryption algorithm involves longer keys. This is why, of the two types of encryption, asymmetric encryption is considered slower but more secure.
Hybrid Encryption: Symmetric + Asymmetric Encryption
Both encryption methods, as we saw, have their own advantages as well as disadvantages. So, what if we create a system that has the advantages of both? Well, it’s certainly possible. In many applications, symmetric and asymmetric encryption methods are used together — security sockets layer (SSL)/transport layer security (TLS) cryptographic protocols being the foremost of them.
In SSL/TLS certificates, first, the identity verification is done utilizing asymmetric encryption. Once the identity of the server has been verified, the encryption process happens using ephemeral symmetric encryption keys. This way, security risks of symmetric encryption and performance/speed issues of asymmetric encryption can be mitigated. Cool, isn’t it?
Symmetric vs. Asymmetric Encryption
| Symmetric Encryption | Asymmetric Encryption |
| Uses a single key to encrypt and decrypt the data. | Uses two separate keys for encryption and decryption. They’re known as “public key” and “private key.” |
| Is more straightforward and conventional method of encryption. | Was invented to mitigate the risks of symmetric encryption and is more complicated. |
| Is faster when compared to asymmetric encryption, thanks to its simplicity. | Is slower and requires more computational power because of its complexity. |
| Requires smaller key lengths, usually of 128-256 bit length. | Asymmetric keys are longer in their lengths. |
| Provides the confidentiality of the data (data security). | Provides confidentiality, authenticity, and non-repudiation. |
| Is useful for encrypting a large amount of data. | Is useful for encrypting a small amount of data. |
| Standard symmetric encryption algorithms are RC4, AES, DES, 3DES, and QUAD. | Standard asymmetric encryption algorithms are RSA, Diffie-Hellman, ECC, El Gamal, and DSA. |


Comments
Post a Comment