AES vs DES encryption
AES vs DES encryption algorithm
What Is a Symmetric Block Cipher?
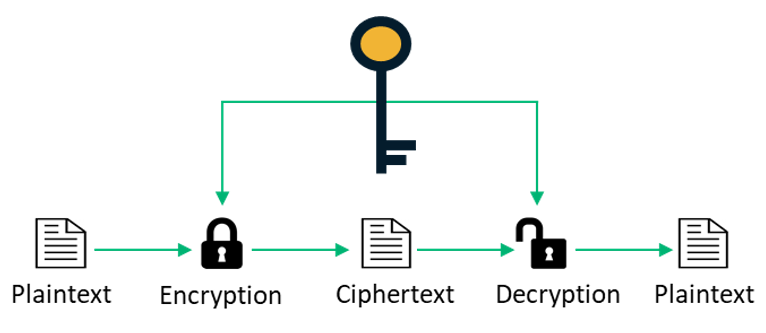
To know what DES vs AES actually means, you first need to understand what a symmetric block cipher is. Also known as symmetric encryption algorithm, a block cipher is a cryptographic algorithm that turns plaintext data into encrypted text (also known as ciphertext). To give you an example, a block cipher might turn “Apple” into something like “2e$5kv7fg*=v#.”
The transformation from plaintext to ciphertext is carried out using what’s known as a symmetric encryption key, which is a mathematical function. Basically, upon applying this key, the plaintext is turned into blocks of a certain size that are then encrypted. Because it’s a symmetric key, it can also decrypt the encrypted text, which reverts it to its original form.
Modern block ciphers:
- Are fast and can process vast amounts of data. Because they’re able to handle this better than asymmetric encryption algorithms, it makes great for use in enterprises when you’re encrypting data at scale.
- Use a substitution and transposition function. This complex series of processes that involves swapping out individual characters and blocks of ciphertext results in more secure ciphertext at the end of the process.
I hope this provided you with a greater understanding of symmetric block ciphers. Now, let’s jump into the first part you’re here for when learning about DES vs AES: the DES algorithm.
What Is the DES Symmetric Encryption Algorithm?
DES, which stands for data encryption standard, is a symmetric block cipher/encryption algorithm that operates on a key length of 56-bits. DES was developed in the early 1970s by IBM for the protection of sensitive, unclassified electronic government data. The final version of DES was published as an official Federal Information Processing Standard (FIPS) for the United States in 1977.
IBM created this algorithm based on the Feistel Structure, which was designed by a cryptographer named Horst Feistel. In this approach, the whole plaintext data as a whole is divided into two parts, and the encryption process is applied to each element individually. As DES works on a 64-bit input, the plaintext is divided into two parts of 32-bit each. Then, each part is supposed to undergo 16 “rounds” of operation, and 64-bit encrypted text is produced as output. The encryption process involves several important steps:
- Expansion — This refers to an increase in message length when it’s encrypted.
- Permutation and substitution — Substitution replaces plaintext letters by letters or numbers or symbols. Permutation rearranges their order in plaintext.
- XOR operation with a round key — This refers to an encryption method that’s based on the Boolean algebra function XOR.
Why DES Isn’t Secure to Use
To better understand DES vs AES — and why one it in use when the other is not — definitely pay attention here. The approval of DES to protect the U.S. government’s sensitive information resulted in speedy and widespread adoption around the world. However, this also led to greater scrutiny about this encryption algorithm. One of the main reasons behind this concern was its shorter key length.
To test the security of the DES algorithm, many challenges were initiated to see whether the algorithm could be broken, which would leave any encrypted data vulnerable to exposure:
- The first challenge (DES I contest, 1997) took 84 days.
- The second challenge (DES II, 1998) took a month.
- The last one (DES III) took only 22 hours and 15 minutes to break through the DES algorithm.
As a result of all of this, DES was viewed as being an insecure algorithm and became officially deprecated by the National Institute of Standards and Technology (NIST) in 2005. DES, which was a part of TLS 1.0 and 1.1 protocols, was discontinued in TLS 1.2.
The Emergence of Triple DES (3DES)
Once the DES algorithm was found to be insecure, triple DES (3DES), also known as the triple data encryption algorithm (TDEA) was introduced in 1999. This version of the DES algorithm, as implied in the name, applies the DES algorithm three times to each data block. This made 3DES more secure than DES, and it became a powerful algorithm used extensively in payment systems, in the finance industry and in cryptographic protocols such as TLS, SSH, IPsec, and OpenVPN.
However, with time, 3DES was also found to be vulnerable based on the Sweet32 vulnerability that was discovered by researchers Karthikeyan Bhargavan and Gaëtan Leurent. This initiated the discussion of deprecating 3DES and, ultimately, NIST announced its retirement in a draft guidance published in 2018. Based on this recommendation, 3DES is to be eliminated from the use of all new applications after 2023. TLS 1.3, the latest standard for SSL/TLS protocols, has also discontinued the use of 3DES, which was a part of the TLS 1.2 protocol.
What Is the AES Symmetric Encryption Algorithm?
If you thought that AES (advanced encryption standard) came as a comparable replacement for DES, then you’re right. AES, which is also known as Rijndael, was developed by two Belgian cryptographers named Vincent Rijmen and Joan Daemen. This encryption algorithm is actually a family of ciphers that are of different key lengths and block sizes. It became an encryption standard on approval by (NIST) almost 20 years ago.
Compared to DES and 3DES, AES offers much better performance —both in terms of speed as well as security. It’s known to perform six times faster than DES. But what makes AES so great? The biggest strength of AES lies in the various key lengths it provides, which enables you to choose between 128-, 192-, and 256-bit keys. The use of AES 256-bit encryption is fairly standard nowadays, and generally speaking in encryption, the longer the key is, the harder it is to crack (and the more secure it is).
As we saw, DES relies on the Feistel network in which the data block is divided into two halves before applying the encryption process. AES, on the other hand, works on the method of substitution and permutation. In AES, the plaintext data is converted into 128-bit blocks, and then the encryption key of 128 bits is applied.
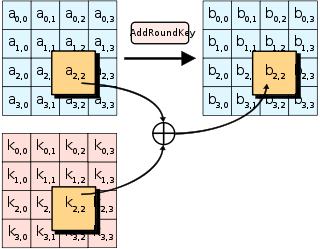
The AES encryption process involves 10 rounds of operation, with each round having its sub-processes that include sub-bytes, shift rows, mix columns, and add round keys. The last round (10th), however, doesn’t include the sub-process of mix columns.
In AES, the higher the number of rounds that are performed, the greater the level of security the encryption affords. The number of rounds applied in the encryption process depends upon the size of the key. For example:
- 10 rounds are included for a 128- bit key,
- 12 rounds for a 192- bit key, and
- 14 rounds for a 256- bit keys.
Is AES Encryption Strong Enough?
When it comes to breaking AES — or most encryption algorithm methods for that matter — there’s only one method to rely on. This method is known as “brute forcing.” In simpler words, it’s a trial-and-error operation that’s performed by computers at a super-fast speed. That’s why, the longer the key length is, the higher the number of possible combinations an attacker will have to brute force to crack it.
When it comes to the security of AES-256, there are 2256 possible combinations. Now that’s a pretty large number. Here’s what it looks like:
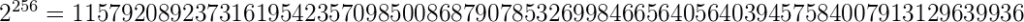
However, that doesn’t mean that AES will remain invincible. Quantum computers, with their qubital superpowers, are expected to break AES encryption. However, there’s no need to worry about it right now as they’re still some years away.
Where Is AES Used?
AES is an extremely potent and efficient method when it comes to encryption of the data. That’s why many agencies — including the National Security Agency (NSA) and other government entities — use AES encryption to protect sensitive information. Apart from that, AES is used as a standard for the following:
- Wireless security
- Processor security & file encryption
- SSL/TLS protocol (website security)
- Wi-Fi security
- Mobile app encryption
- Libraries in software development
- VPN (virtual private network) implementation
DES vs AES: A Side-By-Side Comparison of These Two Symmetric Encryption Algorithms
Yeah, that was a lot of information to try to take in all at once. And, frankly, it can all be a bit confusing if you’re somewhat new to the topic. That’s why we thought it might be helpful to include a side-by-side comparison table to help you see the differences between these two algorithms:
| DES Encryption Algorithm | AES Encryption Algorithm |
| Established as a standard in 1977. | Standardized in 2001. |
| Has the key length of 56 bits. | It offers key lengths of 128, 192, and 256 bits. |
| The block size is 64 bits. | The block size can be of 128, 192, or 256 bits – depending upon the key length. |
| The encryption process is time-consuming. | It offers almost six times faster performance compared to 3DES. |
| The encryption process involves 16 rounds. | The encryption process involves 10, 12, and 14 rounds in the case of 128, 192, and 256 bits, respectively. |
| The original version of DES has been found to be insecure and was deprecated from use in 2005. 3DES, the upgraded version of DES, is currently in use in some applications, but it’s due to be deprecated in 2023. | AES is a much secure symmetric encryption algorithm with no considerable weakness found in it. It’s used worldwide in applications such as hardware, software, SSL/TLS protocols, etc. It’s the current standard of symmetric encryption. |
| It is based on Feistel Cipher Structure. | AES works substitution & permutation principle. |
| An encryption round involves Expansions permutation Xor, S-box, P-box, Xor, and Swap. | Encryption round involves Subtypes, Shiftonce, Mix columns, and Addroundkeys. |
Final Thoughts: Our Two Cents on DES vs AES
When it comes to the DES vs. AES debate, there’s only one winner. That’s why all modern day applications rely on AES instead of the DES encryption algorithm for secure encryption. However, that doesn’t mean that you’re not using DES. According to SSL Labs, an estimated 2.5% of websites are still using TLS 1.0 and 1.1 protocols, which consist of the insecure DES algorithm.


Comments
Post a Comment